Five Possible Levels of Analysis of a Knowledge Graph
Jun 30 2023
| Level of Analysis |
|
||||||||||
| Concept |
|
||||||||||
| Relationship |
|
||||||||||
| Model |
|
||||||||||
| Theme |
|
||||||||||
| Theory |
|
Examples of Knowledge Analytics
This appendix illustrates possible analyses of digitized knowledge, i.e., potential use cases of the search and analysis app (Analysaurus).
Querying is based on openCypher (Francis et al. 2018), an industry standard for querying graph databases[1], and R is used for further processing of query results.
Element Level: At the element level, we can measure the semantic similarity of elements using NLP methods. For example, Table A.1 shows three different semantic similarity measures of concepts based on their labels (Song et al. 2021b).
| Concept 1 | Concept 2 | String-based(Cosine; Jaccard) | Corpus-based(Latent semantic analysis) | Knowledge-based (Wordnet) |
| Internet privacy concerns | User privacy concerns | 0.667 | 0.999 | 1 |
| Information privacy concerns | Privacy concern | 0.408 | 0.998 | 1 |
| Risks | Costs | 0 | 0.998 | 0.167 |
| Trust | Work overload | 0 | 0 | 0.133 |
| Costs | Benefits | 0 | 0.615 | 0.308 |
In a body of literature, it is quite common to have multiple definitions for the same concept. However, when knowledge is digitized, concept similarity computation is possible (see Table A.2 for the example of trust).
The similarity of concept definitions can be computed using NLP tools such as BERT. Inspection of Table A.3 reveals that definition 3 has the highest average similarity score and the most similar definitions are 1 and 5 (bold), while the least similar are 1 and 7, and 5 and 7 (italics).
| Definition | Publication | |
| 1 | We define trust as the subjective assessment of one party that another party will perform a particular transaction according to his or her confident expectations, in an environment characterized by uncertainty. | Ba, S., & Pavlou, P. A. (2002). Evidence of the Effect of Trust Building Technology in Electronic Markets: Price Premiums and Buyer Behavior. MIS Quarterly, 26(3), 243. |
| 2 | Trust is argued to be rooted in perceptions of teammates’ ability, benevolence, and integrity (Jarvenpaa et al. 1998). Ability refers to the aptitude and skills that enable an individual to be perceived as competent by teammates (Jarvenpaa et al. 1998; Mayer et al. 1995). Benevolence refers to the extent to which an individual is believed to be willing to help teammates beyond personal motives or individual gain. 1995). Integrity refers to the extent to which an individual is believed to adhere to a set of principles thought to make her dependable and reliable. | Piccoli, & Ives. (2003). Trust and the Unintended Effects of Behavior Control in Virtual Teams. MIS Quarterly, 27(3), 365. |
| 3 | Trust is defined as the buyer’s intentions to accept vulnerability based on her beliefs that the transaction will meet her confident expectations. | Pavlou, Liang, & Xue. (2007). Understanding and Mitigating Uncertainty in Online Exchange Relationships: A Principal-Agent Perspective. MIS Quarterly, 31(1), 105. |
| 4 | The user beliefs in the recommendation agents’ competence, benevolence, and integrity. The beliefs that 1) the recommendation agent has the ability, skills, and expertise to perform effectively 2) the recommendation agent cares about the user and acts in the user’s interest 3) the recommendation agent adheres to a set of principles (e.g., honesty and promise keeping) that the user finds acceptable, | Xiao, & Benbasat. (2007). E-Commerce Product Recommendation Agents: Use, Characteristics, and Impact. MIS Quarterly, 31(1), 137. |
| 5 | Trust reflects one party’s belief that its requirements will be fulfilled through future actions undertaken by the other party. | Goo, Kishore, Rao, & Nam. (2009). The Role of Service Level Agreements in Relational Management of Information Technology Outsourcing: An Empirical Study. MIS Quarterly, 33(1), 119. |
| 6 | Trust is conceptualized as a single variable and refers to general confidence in the website. | Cyr, Head, Larios, & Pan. (2009). Exploring Human Images in Website Design: A Multi-Method Approach. MIS Quarterly, 33(3), 539. |
| 7 | The extent to which a buyer perceives in a seller’s ability (i.e., skills, competencies, and characteristics in seller his/her products online), integrity (adhering to a set of principles that the buyer finds acceptable), and benevolence (i.e., doing good toward the buyer). | Ou, C. X., Pavlou, P. A., & Davison, R. M. (2014). Swift Guanxi in Online Marketplaces: The Role of Computer-Mediated Communication Technologies. MIS Quarterly, 38(1), 209–230. |
| Definition | 1 | 2 | 3 | 4 | 5 | 6 | 7 |
| 1 | — | — | — | — | — | — | — |
| 2 | 0.60 | — | — | — | — | — | — |
| 3 | 0.80 | 0.63 | — | — | — | — | — |
| 4 | 0.57 | 0.76 | 0.63 | — | — | — | — |
| 5 | 0.81 | 0.61 | 0.77 | 0.57 | — | — | — |
| 6 | 0.59 | 0.50 | 0.57 | 0.49 | 0.46 | — | — |
| 7 | 0.38 | 0.57 | 0.52 | 0.76 | 0.38 | 0.45 | — |
| Means | 0.62 | 0.61 | 0.66 | 0.63 | 0.60 | 0.51 | 0.58 |
Element-Relationship Level: Visualizations can be generated to focus on a particular element and its role. For example, the antecedents of trust can be seen in Figure A.1.
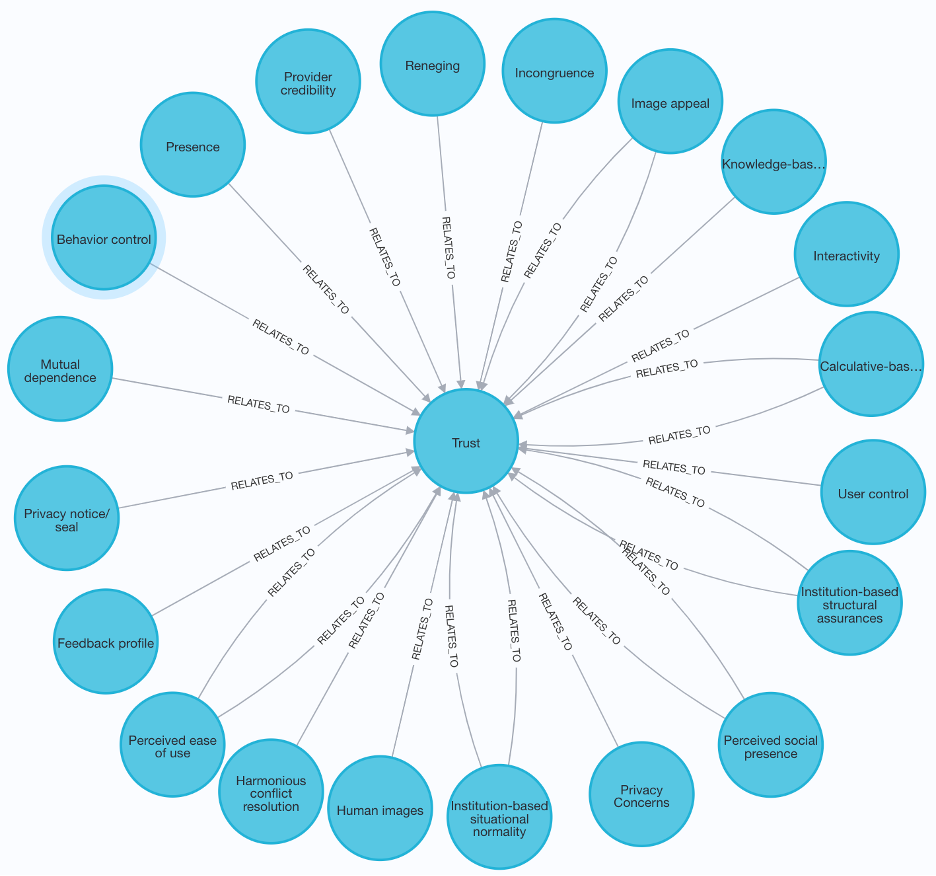
Figure 1 Antecedents of Trust
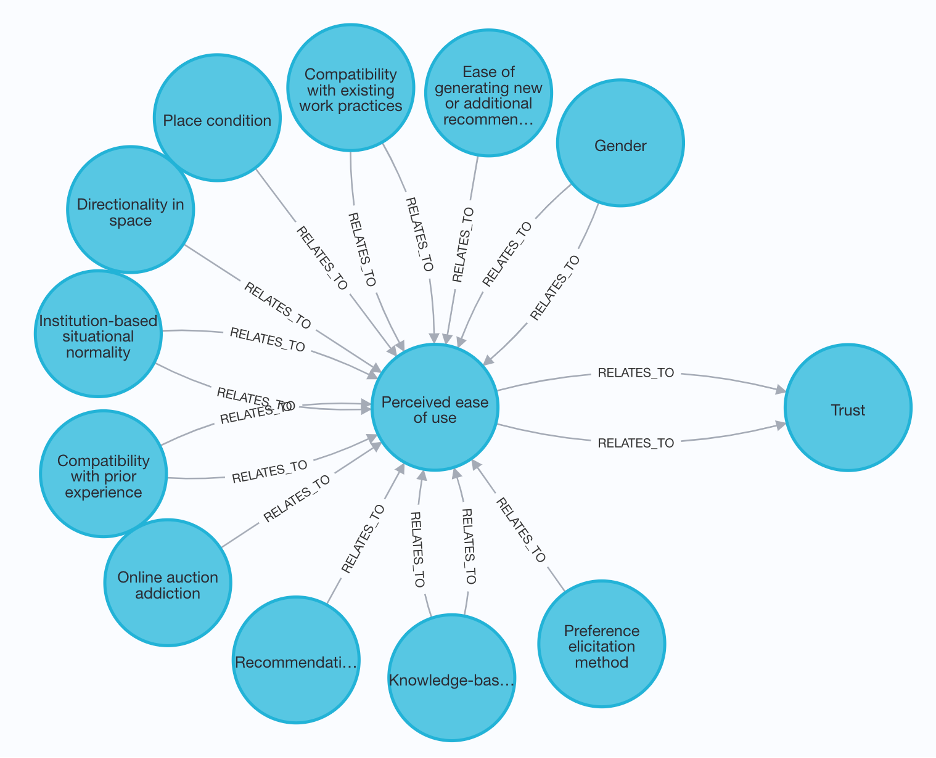
Figure 2 Causal chain – antecedents of antecedents
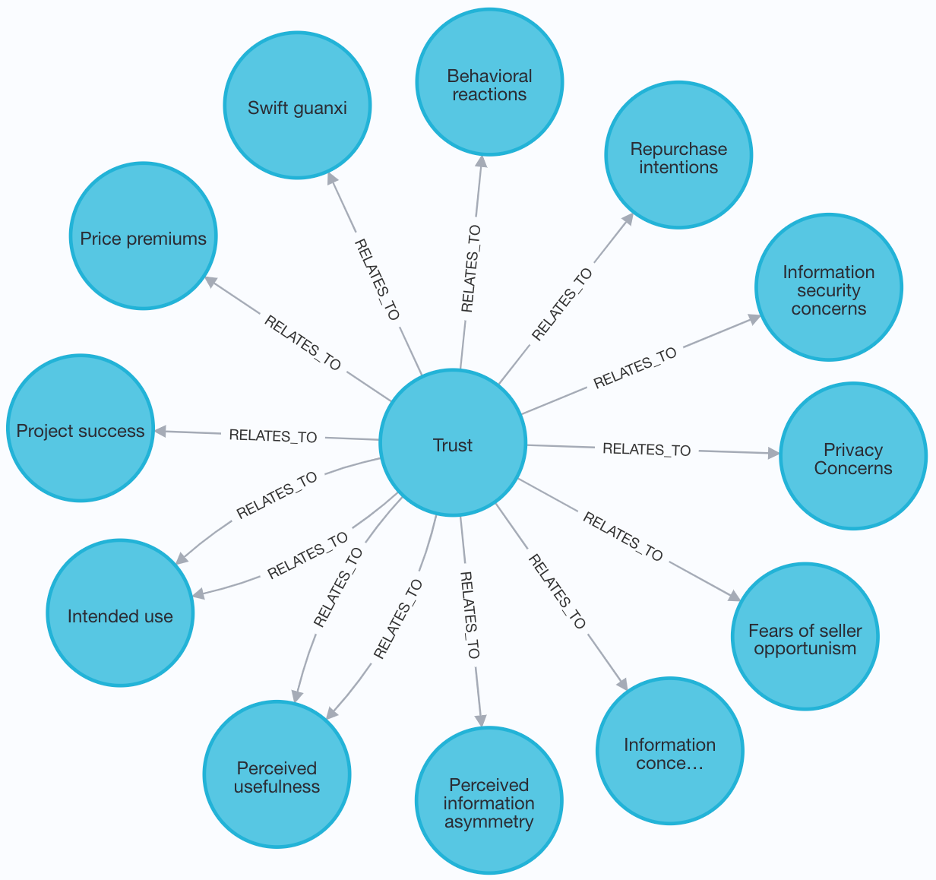
Figure 3 Consequents of Trust
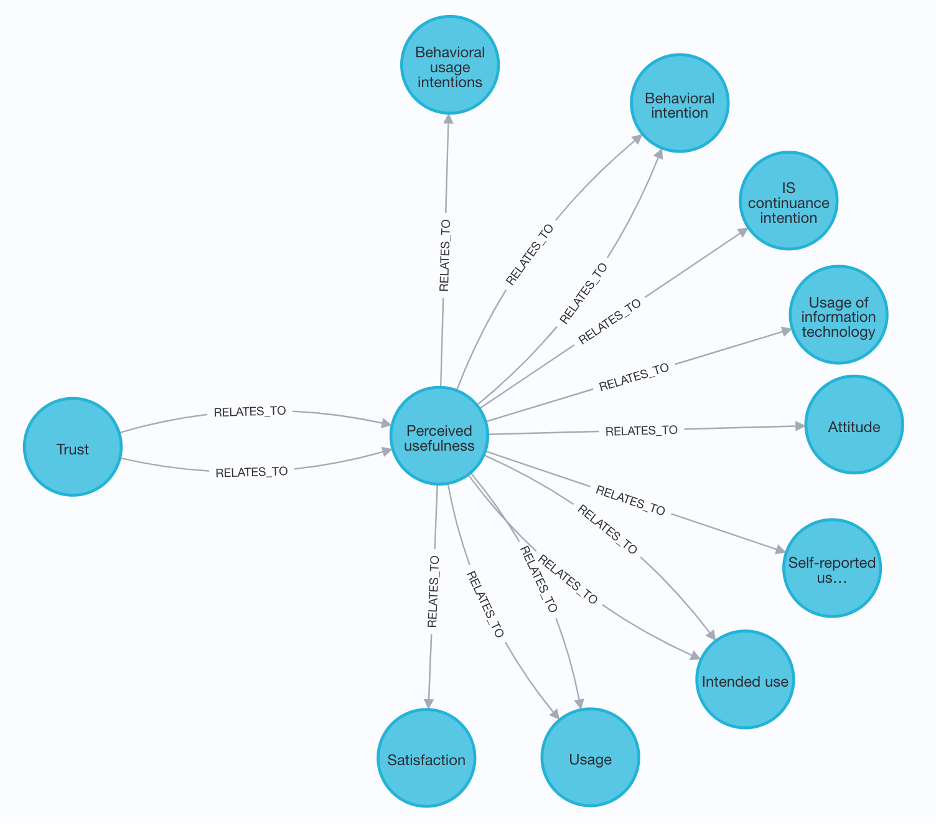
Figure 4 Causal chain – consequents of consequents
Social network analysis can holistically assess the importance of an element in a knowledge network (see Table A.5). Specifically:
A high Betweenness centrality suggests that an element is an influential mediator.
A high Closeness centrality aggregates the most direct causal influence that an element has on other elements in a knowledge network.
A high Outdegree centrality of an element in a knowledge network indicates that an element is a fundamental antecedent.
A high Indegree centrality score signals that an element is a commonly accepted consequent.
|
Betweenness centrality |
Out-degree centrality |
In-degree centrality |
|
Trust |
Work status |
Performance |
|
Gender |
Computer self-efficacy |
Trust |
|
Habit |
Work exhaustion |
Usage |
|
Perceived usefulness |
Trust |
Turnover intention |
|
Satisfaction |
Gender |
Work exhaustion |
|
Information privacy concerns |
Role ambiguity |
Job satisfaction |
|
Behavioral intention |
Information privacy concerns |
Perceived usefulness |
|
Privacy Concerns |
Job autonomy |
IT use |
|
Group’s adoption of the technology |
Perceived usefulness |
Behavioral intention |
|
Group valence toward the technology |
Computer support |
Quality of knowledge exchanged |
Table 15 Concepts with Highest Network Centrality Measures
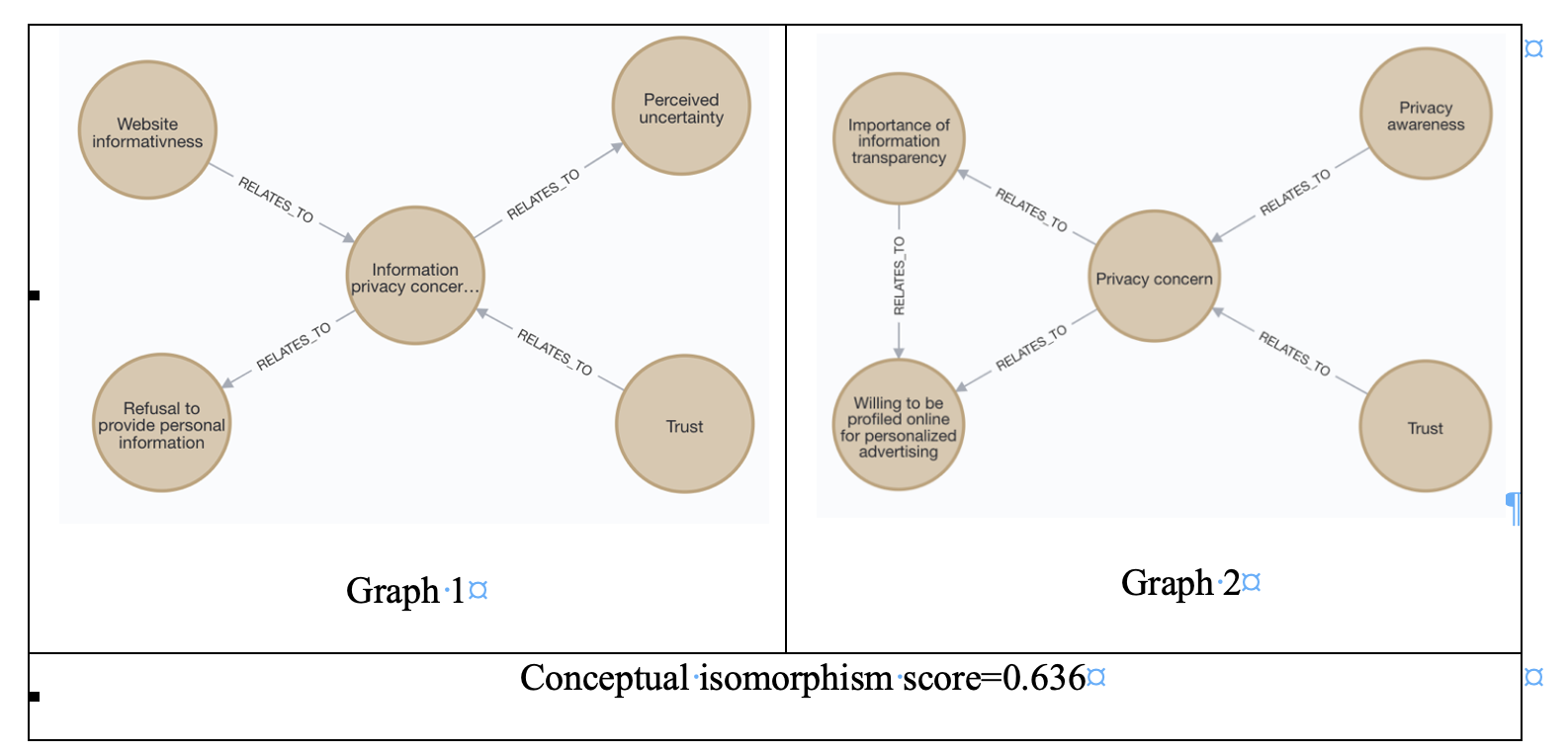
Model Level: Similarity can be computed for any pair of causal models for a domain of interest. Figure A.2 shows two privacy models and their conceptual isomorphism score, a measure between 0 and 1 (Song et al. 2021b).
Theory Level: Theories guide knowledge creation. For the MISQ trust curation (Söllner et al. 2016), there is a wide variety of theoretical foundations, which could suggest that there is little coalescence around theories for explaining trust formation (see Table A.6).
|
Theory |
Curations |
Number of curations |
|
Agency theory |
IS Control and Governance; IS Sourcing; Information Privacy; IT Project Management; Trust |
5 |
|
Theory of planned behavior |
IS Control and Governance; IT Workforce; IT Project Management; Securing Digital Assets; Trust |
5 |
|
Adaptive structuration theory |
IT-supported Collaboration; Health Information Technology; IS Use; Trust |
4 |
|
Institutional theory |
Health Information Technology; IS Sourcing; IS Use; Securing Digital Assets |
4 |
|
Prospect theory |
IS Control and Governance; IT Workforce; Information Privacy; IT Project Management |
4 |
|
Relational exchange theory |
IS Control and Governance; IS Sourcing; IT Project Management; Trust |
4 |
|
Social exchange theory |
IS Sourcing; IT Workforce; Knowledge Management; Trust |
4 |
|
Social presence theory |
IT-supported Collaboration; IS Use; Information Privacy; Trust |
4 |
|
Structuration theory |
IS Alignment; IT-supported Collaboration; Health Information Technology; IS Use |
4 |
|
Theory of reasoned action |
IS Use; Knowledge Management; Securing Digital Assets; Trust |
4 |